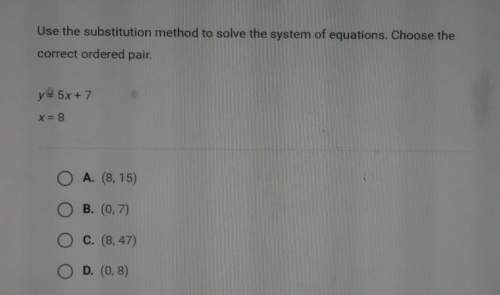
Mathematics, 23.07.2019 05:30 elenasoaita
Review the excerpt from the code book. if eve parks a van outside alice's house, she can use sensitive tempest equipment to identify each individual keystroke that alice makes on her computer. this would allow eve to intercept the message as it is typed into the computer, before it is encrypted. to defend against tempest attacks, companies are already supplying shielding material that can be used to line the walls of a room to prevent the escape of electromagnetic signals. in this excerpt, the author explains why computers are easily stolen. why keyboards are unsanitary. how computer security can be broken. how friends share secret messages.

Answers: 2


Other questions on the subject: Mathematics

Mathematics, 21.06.2019 16:00, aidengalvin20
Plz i beg u asap ! what is the equation of this graphed line? enter your answer in slope-intercept form in the box.
Answers: 2

Mathematics, 21.06.2019 17:50, amcdonald009
To solve the system of equations below, grace isolated the variable y in the first equation and then substituted into the second equation. what was the resulting equation? 3y=12x x^2/4+y^2/9=1
Answers: 1

Mathematics, 21.06.2019 18:00, glocurlsprinces
The longer leg of a 30° 60° 90° triangle is 16 times square root of three how long is a shorter leg
Answers: 1

Mathematics, 21.06.2019 22:30, lilmaddy8856
Which expressions equal 9 when x=4 and y=1/3 a. x2+6y b. 2x + 3y c. y2-21x d. 5 (x/2) -3y e. 3x-9y
Answers: 2
You know the right answer?
Review the excerpt from the code book. if eve parks a van outside alice's house, she can use sensiti...
Questions in other subjects:

Mathematics, 03.02.2020 06:50





Mathematics, 03.02.2020 06:50