Computers and Technology, 01.08.2019 16:20 kelyanthecrafte
U2- an example of is an attempt by an unauthorized user to gain access to a system by posing as an authorized user.

Answers: 1


Other questions on the subject: Computers and Technology

Computers and Technology, 21.06.2019 22:00, rosetoheart2
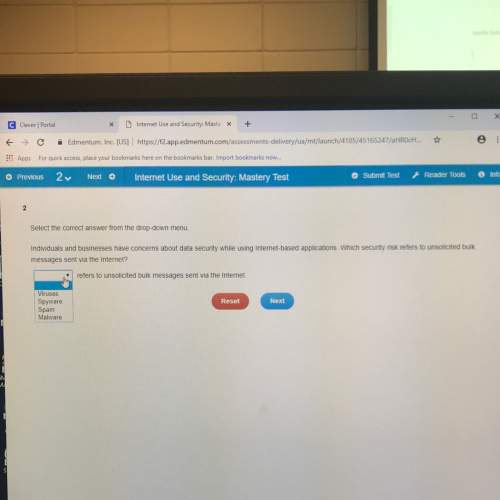
What do the principles of notice, choice, onward transfer, and access closely apply to? a. privacyb. identificationc. retentiond. classification
Answers: 1

Computers and Technology, 22.06.2019 15:30, tfornwalt4390
Melissa needs to add a topic to an email that she will send to her teacher. choose the name of the field where she should type her topic.
Answers: 2

Computers and Technology, 23.06.2019 15:00, herchellann302
To check whether your writing is clear , you can
Answers: 2

Computers and Technology, 24.06.2019 19:20, boyancecristina
Which command suppresses the visibility of a particular row or column in a worksheet?
Answers: 1
You know the right answer?
U2- an example of is an attempt by an unauthorized user to gain access to a system by posing as an...
Questions in other subjects:




Mathematics, 02.09.2019 01:00



Biology, 02.09.2019 01:00