Which scenarios describe unethical e-mail practices?
...

Computers and Technology, 06.02.2022 14:00 krishawnnn
Which scenarios describe unethical e-mail practices?
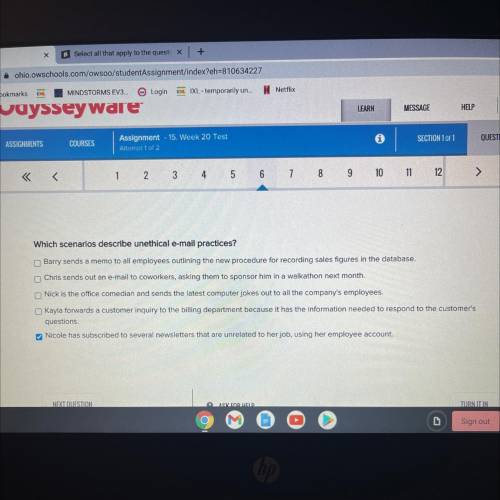

Answers: 3


Other questions on the subject: Computers and Technology

Computers and Technology, 21.06.2019 16:20, daniecott
Quincy would like to view the contents of a specific message in his inbox. a portion of his computer screen is shown. what should quincy do in order to complete this task? 1. click on the inbox in the navigation pane, and click on the specific message in the folder pane to display its contents. 2. click on the inbox in the outlook today window, and click on the specific message in the folder pane to display its contents. 3. double-click the message’s header in the outlook today window, and right-click on the specific message to display its contents. 4. double-click the mail option in the navigation pane, and right-click on the specific message to display its contents.
Answers: 1

Computers and Technology, 21.06.2019 23:00, xxbriannahollandxx
In a file-oriented information system, a work file stores relatively permanent data about an entity is created and saved for backup and recovery purposes stores records that contain day-to-day business and operational data is a temporary file created by an information system for a single task
Answers: 1

Computers and Technology, 24.06.2019 15:20, 710jonathan
Local area networks use many of the same network technologies and the internet, only on a smaller scale. devices that access lans are equipped with a network interface that contains circuitry for wireless or wired connections. devices also have a physical address, in addition to the ip addresses acquired from a dhcp server. the most popular wired technology is . the most popular wireless technology is , which can be configured as a(n) or star topology. setting up a lan and configuring its router is fairly easy. the first step is to change the standard to one that is secure. next, create a(n) that uniquely identifies the network by name. it is also important to activate wireless to prevent wireless signals from being intercepted during transmission. a limited-access network can be created for visitors to use. by activating , the router will be able to assign ip addresses to each device that joins the network. to connect to a secure lan that is protected by encryption, an encryption , or password, is required. lans can be used to access data collected by iot devices and the networks that tie these devices together. technologies such as rfid, nfc, bluetooth smart, zigbee, and z-wave offer -power links, essential for battery-powered devices that can’t expend excess amounts of energy transmitting data.
Answers: 1

Computers and Technology, 24.06.2019 18:30, trevorhenyan51
Dereck works for long hours on his computer. he frequently experiences physical strain by the end of the day because he does not follow an important rule of ergonomics with respect to the use of keyboards. which of the following actions of dereck could lead to physical strain? a. placing the keyboard exactly in front of him while typingb. keeping hands and wrists straight while typingc. using wrist pads throughout the dayd. pounding at the keys on the keyboard while typinge. resting his hands on the keyboard when he is not typing
Answers: 1
You know the right answer?
Questions in other subjects:












