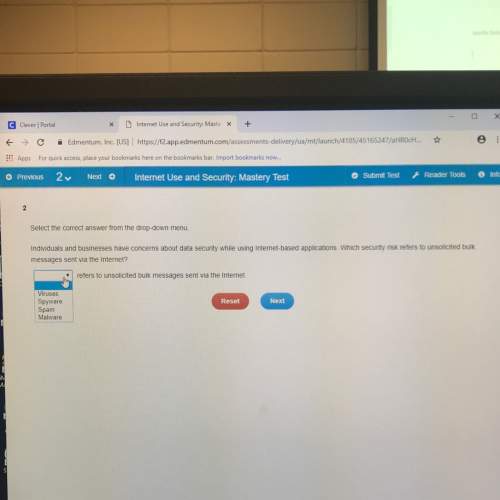
Computers and Technology, 16.08.2021 23:00 lizzie3545
An internal penetration tester finds a legacy application that takes measurement input made in a text box and outputs a specific string of text related to industry requirements. There is no documentation about how this application works, and the source code has been on Which of the following would BEST allow the penetration tester to determine the input and output relationship?
a. Running an automated fuzzer
b. Constructing a known cipher text attack
c. Attempting SQL injection commands
d. Performing all packet capture
e. Using the application in a malware sandbox

Answers: 3


Other questions on the subject: Computers and Technology

Computers and Technology, 21.06.2019 18:00, chaofails
Jenna updated her status on a social network regarding her upcoming vacation. what information should jenna not provide when updating her status on a social networking site? a. her favorite quote b. her likes in popular culture c. her routine d. her opinions on social issues res
Answers: 1

Computers and Technology, 22.06.2019 20:00, manyah6189
Amanda needs to create an informative print brochure for her local library’s fundraiser dinner. what critical detail must she have before she starts designing the brochure?
Answers: 1


Computers and Technology, 23.06.2019 06:30, QueeeenUknown7437
How do you write an argumentative essay about the importance of free enterprise ?
Answers: 1
You know the right answer?
An internal penetration tester finds a legacy application that takes measurement input made in a tex...
Questions in other subjects:





Mathematics, 21.02.2020 05:16


History, 21.02.2020 05:16

English, 21.02.2020 05:16


Mathematics, 21.02.2020 05:16