Computers and Technology, 03.06.2021 02:00 sksksjs
The most serious security threat to Bluetooth-enabled devices is , which occurs when a hacker gains access to the device and its functions without the owner's consent.

Answers: 3


Other questions on the subject: Computers and Technology

Computers and Technology, 23.06.2019 15:20, manarhizam12
An ou structure in your domain has one ou per department, and all the computer and user accounts are in their respective ous. you have configured several gpos defining computer and user policies and linked the gpos to the domain. a group of managers in the marketing department need different policies that differ from those of the rest of the marketing department users and computers, but you don't want to change the top-level ou structure. which of the following gpo processing features are you most likely to use? a, block inheritance b, gpo enforcement c, wmi filtering d, loopback processing
Answers: 3


Computers and Technology, 25.06.2019 13:30, abigailguzman4108
Peripherals can be used to output information. true or false
Answers: 1
You know the right answer?
The most serious security threat to Bluetooth-enabled devices is , which occurs when a hacker gains...
Questions in other subjects:


Mathematics, 26.03.2021 02:20

Geography, 26.03.2021 02:20

Social Studies, 26.03.2021 02:20





Business, 26.03.2021 02:20

Mathematics, 26.03.2021 02:20

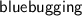 , which occurs when a hacker gains access to the device and its functions without the owner's consent.
, which occurs when a hacker gains access to the device and its functions without the owner's consent.