
Computers and Technology, 27.05.2021 14:00 zero101
Answer following queries :
1- Determine (display) ClientNo of Renters, who have viewed some properties with 3 rooms.
2- Determine (display) ClientNo , fName and lName of Renters, who have viewed all properties with 3 rooms.
3- Determine (display) ClientNo , fName and lName of Renters, who have viewed some properties with 3 rooms.
4- List full details about all properties with 5 rooms and which are allocated in branch office in Glasgow city.
5- List staffNo , fName and lName of staff, who are not responsible for any properties for rent.

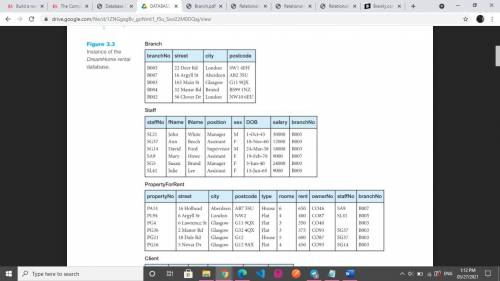

Answers: 2


Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 12:50, michaelchavez6959127
You have just been hired as an information security engineer for a large, multi-international corporation. unfortunately, your company has suffered multiple security breaches that have threatened customers' trust in the fact that their confidential data and financial assets are private and secured. credit-card information was compromised by an attack that infiltrated the network through a vulnerable wireless connection within the organization. the other breach was an inside job where personal data was stolen because of weak access-control policies within the organization that allowed an unauthorized individual access to valuable data. your job is to develop a risk-management policy that addresses the two security breaches and how to mitigate these risks. requirementswrite a brief description of the case study. it requires two to three pages, based upon the apa style of writing. use transition words; a thesis statement; an introduction, body, and conclusion; and a reference page with at least two references. use a double-spaced, arial font, size 12.
Answers: 1

Computers and Technology, 24.06.2019 13:30, elviaortiz402373
Which of the following is not a “fatal four” event?
Answers: 2

Computers and Technology, 24.06.2019 17:50, connorwbrown07
Acontact list is a place where you can store a specific contact with other associated information such as a phone number, email address, birthday, etc. write a program that first takes in word pairs that consist of a name and a phone number (both strings). that list is followed by a name, and your program should output that name's phone number.
Answers: 1

Computers and Technology, 25.06.2019 09:00, shalynmincey
What are some of the things many ctsos do for their members ?
Answers: 1
You know the right answer?
Answer following queries :
1- Determine (display) ClientNo of Renters, who have viewed some propert...
Questions in other subjects:







Mathematics, 14.12.2020 19:50

Arts, 14.12.2020 19:50

Mathematics, 14.12.2020 19:50

Mathematics, 14.12.2020 19:50



