
Computers and Technology, 30.09.2019 19:00 weg5309
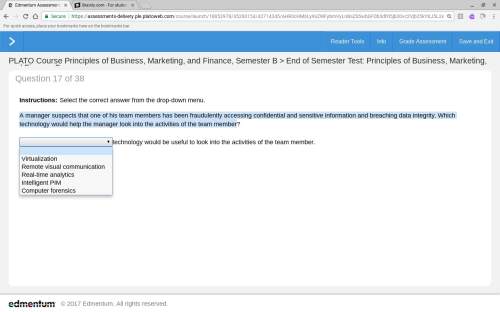
Amanager suspects that one of his team members has been fraudulently accessing confidential and sensitive information and breaching data integrity. which technology would the manager look into the activities of the team member?

Answers: 2


Other questions on the subject: Computers and Technology

Computers and Technology, 21.06.2019 22:00, haydonmetzger
Which one of the following identifies the primary a purpose of information classification processes? a. define the requirements for protecting sensitive data. b. define the requirements for backing up data. c. define the requirements for storing data. d. define the requirements for transmitting data.
Answers: 2


Computers and Technology, 23.06.2019 06:30, jayjay5246
Which option correctly describes a dbms application? a. software used to manage databases b. software used to organize files and folders c. software used to develop specialized images d. software used to create effective presentations
Answers: 1

Computers and Technology, 23.06.2019 08:30, mai1261
Helen's credit card has an apr of 15.32% and a grace period of 17 days and helen pays her balance in the full every month. if her last billing cycle ended on september 26, 2009, and she made her payment on october 11, 2009, did she owe any interest on her last statement's balance?
Answers: 3
You know the right answer?
Amanager suspects that one of his team members has been fraudulently accessing confidential and sens...
Questions in other subjects:

Mathematics, 16.10.2020 08:01




Mathematics, 16.10.2020 08:01

History, 16.10.2020 08:01



Mathematics, 16.10.2020 08:01

History, 16.10.2020 08:01



