Computers and Technology, 24.10.2019 21:43 atefah88
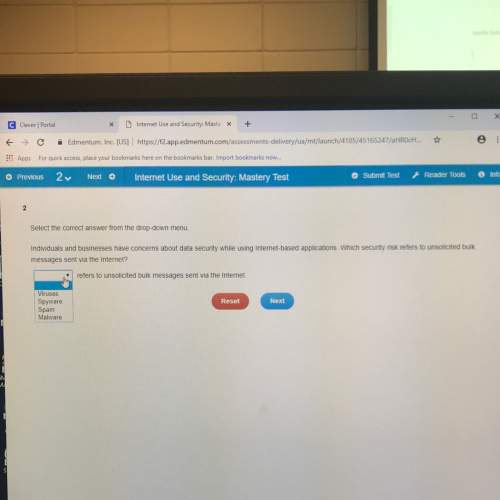
Which of the following is a type of software or hardware that you can use to protect your computer from security threats? firewall virus malware spyware

Answers: 3


Other questions on the subject: Computers and Technology

Computers and Technology, 21.06.2019 20:00, jwagner2277
If you embed a word table into powerpoint, what happens when you make edits to the embedded data? a. edits made to embedded data change the data in the source file; however, edits made to the source file will not be reflected in the embedded data. b. edits made to embedded data don't change the data in the source file; however, edits made to the source file will be reflected in the embedded data. c. edits made to embedded data don't change the data in the source file, nor will edits made to the source file be reflected in the embedded data. d. edits made to embedded data will change the data in the source file, and edits made to the source file will be reflected in the embedded data.
Answers: 1

Computers and Technology, 22.06.2019 10:40, pbarbee3034
Nims is applicable to all stakeholders with incident related responsibilities. true or false
Answers: 1

Computers and Technology, 23.06.2019 04:31, legendman27
Jennifer has to set up a network in a factory with an environment that has a lot of electrical interference. which cable would she prefer to use? jennifer would prefer to use because its metal sheath reduces interference.
Answers: 1
You know the right answer?
Which of the following is a type of software or hardware that you can use to protect your computer f...
Questions in other subjects:

History, 23.02.2021 14:00



Mathematics, 23.02.2021 14:00

Computers and Technology, 23.02.2021 14:00


Chemistry, 23.02.2021 14:00

Mathematics, 23.02.2021 14:00

Computers and Technology, 23.02.2021 14:00

Mathematics, 23.02.2021 14:00