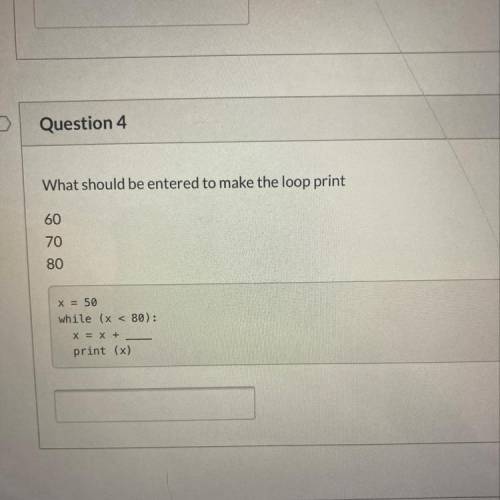
4.2 lesson practice help plzs last one
...

Computers and Technology, 04.11.2020 22:10 xaniawashington
4.2 lesson practice help plzs last one

Answers: 3


Other questions on the subject: Computers and Technology

Computers and Technology, 21.06.2019 16:50, jaueuxsn
3(c). is the following command correct? if not, correct the syntax and explain your answers. you can just rewrite/correct only the wrong parts. (4) select p#, city, zipcode, count(*) from client c, property p, viewing v where c. c# = v. c# and v. p# = p. p# group by p#, city having count(*) > 3;
Answers: 1

Computers and Technology, 22.06.2019 01:00, labrandonanderson00
Ap practice - performance task response the ap create performance task asks you to write about an abstraction that you developed and wrote into your code. most of the time that means identifying a function or procedure you wrote to "manage complexity" in your program. here is the actual prompt from the create performance task: 2d. capture and paste a program code segment that contains an abstraction you developed individually on your own (marked with a rectangle). this abstraction must integrate mathematical and logical concepts. explain how your abstraction manage the complexity of your program. (must not exceed 200 words) below is a segment of code from an "under the sea" program with a rectangle drawn around a portion of the code identifying an abstraction. imagine that you wrote this and are composing an ap response about how this abstraction manages complexity. (note: ignore the requirement that the abstraction integrate "mathematical and logical concepts" for this practice response. just write about managing complexity). explain how the abstraction marked with the rectangle in the code above manage complexity of this program. write your response here submit
Answers: 2

Computers and Technology, 22.06.2019 03:50, TheViperMlg23676
You are working as a security analyst in a company xyz that owns the whole subnet range of 23.0.0.0/8 and 192.168.0.0/8. while monitoring the data, you find a high number of outbound connections. you see that ip's owned by xyz (internal) and private ip's are communicating to a single public ip. therefore, the internal ip's are sending data to the public ip. after further analysis, you find out that this public ip is a blacklisted ip, and the internal communicating devices are compromised. what kind of attack does the above scenario depict?
Answers: 3

Computers and Technology, 22.06.2019 06:30, westjayson69
Requirement types discussed during software development include functional and color scheme nonfunctional and code style constraint and nonfunctional fashionable and functional.
Answers: 2
You know the right answer?
Questions in other subjects:

Mathematics, 19.03.2020 21:05




Mathematics, 19.03.2020 21:05








