
Computers and Technology, 10.09.2020 04:01 Emorej22
. (a) Prove or disprove carefully and in detail: (i) Θ is transitive and (ii) ω is transitive. (b) Assume n is a positive integer. Algorithm A(n: int) int z = 0; int temp = 0; for (int i = 0; i < n ; i++) { for (int j = 0 ; j < i ; j++) { int temp = i + j ; int z = z + temp; } } System. out. println(z) ; What is the input size for Algorithm A? Analyze carefully and explicitly the time complexity of A in terms of the input size. Show all steps. Is A a polynomial time algorithm? Justify your answer.

Answers: 3


Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 23:50, Emptypockets451
You need to design a circuit that implements the functions in the following table: s0 s1 function0 0 a + 10 1 a – b1 0 a + b1 1 a – 1s0 and s1 are 1-bit control inputs to select the function of the circuit. inputs a and b are 4-bitnumbers in 2s complement form. the output is also a 4-bit number in 2s complement form. you are allowed to use only one ttl 7483 4-bit adder to implement all the functions. but anynumber of other components (except the adder) can be used. hint: design a combinational logic circuit to modify the input b and the “carry input” of theadder depending on the control inputs s0 and s1.important: lab grade will depend on the working of the circuit & will be checked of by your labinstructor.1. is the output valid for the following input combinations: a. s0 = 0, s1 = 0, a = 7, b = 3? b. s0 = 0, s1 = 1, a = 7, b = 3? c. s0 = 1, s1 = 0, a = -4, b = -5? d. s0 = 1, s1 = 1, a = -8, b = 6? 2. what is the range of inputs (for both a and b) that will produce the valid output for all the functions?
Answers: 3

Computers and Technology, 23.06.2019 14:30, rose6038
Select the correct answer. peter has launched a website that features baby products. however, clients often find they are unable to access the website because the server is down. which feature of cybersecurity should peter focus on for his website? a. data authenticity b. data privacy c. data availability d. data integrity e. data encryption
Answers: 3

Computers and Technology, 24.06.2019 00:30, rustjallison9928
Asecurity policy is a a. set of guidlines b. set of transmission protocols c. written document d. set of rules based on standards and guidelines
Answers: 2

Computers and Technology, 24.06.2019 22:00, ivethzurita0425
What is a number system, and what is the total number of digits used in this system called? a number system is a system that uses different (options: a) numbers b) symbols c) codes d) digits e) alphabets) to represent different numbers. the total number of digits used in a number system is known as its (options: 1) processor 2) converter 3) radix 4) least significant digit 5) most significant digit)
Answers: 1
You know the right answer?
. (a) Prove or disprove carefully and in detail: (i) Θ is transitive and (ii) ω is transitive. (b) A...
Questions in other subjects:

Mathematics, 13.09.2020 20:01

Mathematics, 13.09.2020 20:01

Mathematics, 13.09.2020 20:01

Mathematics, 13.09.2020 20:01

Mathematics, 13.09.2020 20:01

Mathematics, 13.09.2020 20:01

Mathematics, 13.09.2020 20:01

Mathematics, 13.09.2020 20:01

English, 13.09.2020 20:01

Mathematics, 13.09.2020 20:01

 is transitive, which means it converts one action to others object because if
is transitive, which means it converts one action to others object because if  indicates
indicates 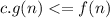 . It's true by definition, that becomes valid. But if
. It's true by definition, that becomes valid. But if 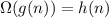 , which implies
, which implies 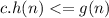 . it's a very essential component. If
. it's a very essential component. If 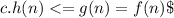 . They
. They 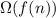 will also be
will also be  .
.  is convergent since the
is convergent since the  . It means they should be dual a and b constant variable, therefore
. It means they should be dual a and b constant variable, therefore 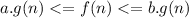 could only be valid for the constant variable, that is
could only be valid for the constant variable, that is  .
. . It is the outside there will be a loop(i) for n iterations, that is also encoded inside it, the for loop(j), which would be a loop
. It is the outside there will be a loop(i) for n iterations, that is also encoded inside it, the for loop(j), which would be a loop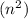 . All internal loops operate on a total number of
. All internal loops operate on a total number of  generations and therefore the final time complexity is
generations and therefore the final time complexity is 

