Computers and Technology, 20.03.2020 04:00 rosas8
Create Player. h and Player. cpp to implement the Player class as described below. You will also need to create a playerDriver. cpp file to test your Player class implementation, but do not include those routines here. The Player class has the following attributes:Data members (private):Data members (private):
string: name The player’s name
double: points The player’s points
Member functions (public):
Default constructor Set name="" and points to value 0.
Parameterized constructor Takes a string and double initializing name and points, in this order
getName() Returns the player’s name as a string
getPoints() Returns the player’s points as a double
setName(string) Sets the player’s name (and returns nothing)
setPoints(double) Sets the player’s points (and returns nothing)
In the Answer Box below, paste your Player class and its implementation (the contents of Player. h and Player. cpp).
Do not have #ifndef or #define.
Do not add #include (or any other headers - they are provided)
Do not add using namespace std;
Do not add main() function
Note that there are some random test cases. These are not edge cases, but rather just randomly generated input values to make sure code is flexible. They're also meant to be mildly entertaining.
For example:
Test Result
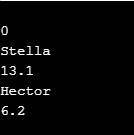
// checking default constructor
Player stella;
cout << stella. getName() << endl;
cout << stella. getPoints() << endl;
0
// checking name setters and getters
Player stella;
stella. setName("Stella");
cout << stella. getName() << endl;
Stella
// checking points setters and getters
Player stella;
stella. setPoints(13.1);
cout << stella. getPoints() << endl;
13.1
// checking parameterized constructor
Player hector("Hector", 6.2);
cout << hector. getName() << endl;
cout << hector. getPoints() << endl;
Hector
6.2

Answers: 2


Other questions on the subject: Computers and Technology

Computers and Technology, 23.06.2019 11:00, jolleyrancher78
What are the possible consequences of computer hacking? what is computer piracy? describe some examples. what are the effects of computer piracy? what are the possible consequences of computer piracy? what is intentional virus setting? describe some examples. what are the effects of intentional virus setting? what are the possible consequences of intentional virus setting? what is invasion of privacy? describe some examples. what are the effects of invasion of privacy? what are the possible consequences of invasion of privacy? what is an acceptable use policy and what is the purpose of the acceptable use policy what is intellectual property and how can you use it?
Answers: 1

Computers and Technology, 23.06.2019 14:30, rose6038
Select the correct answer. peter has launched a website that features baby products. however, clients often find they are unable to access the website because the server is down. which feature of cybersecurity should peter focus on for his website? a. data authenticity b. data privacy c. data availability d. data integrity e. data encryption
Answers: 3

Computers and Technology, 25.06.2019 05:30, pennygillbert
When a game allows you to pick party members from a large pool, each with different classes and roles but in which no single party combination is clearly superior to others, the game is using: intransitive relationships transitive relationships orthogonal relationships parallel relationships
Answers: 1

Computers and Technology, 26.06.2019 02:30, wdgyvwyv8729
Technician a says underinflation of a tire causes excessive one-sided wear on one side of the tread. technician b says overinflation of a tire causes excessive wear on the center portion of the tread. who is correct? tech a tech b both tech a and b neither tech a and b
Answers: 1
You know the right answer?
Create Player. h and Player. cpp to implement the Player class as described below. You will also nee...
Questions in other subjects:




Mathematics, 31.03.2020 23:20

Mathematics, 31.03.2020 23:20


English, 31.03.2020 23:20


Biology, 31.03.2020 23:20

English, 31.03.2020 23:20