Computers and Technology, 26.12.2019 22:31 samavants74
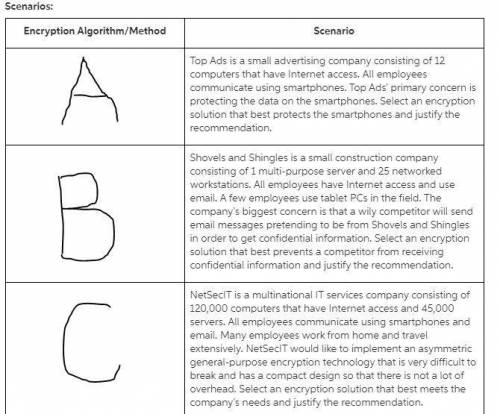
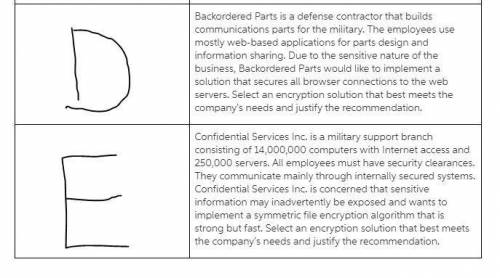
Match common encryption algorithms and methods with the scenarios representing real-world business applications and requirements. you may use the course textbook and the internet to research encryption algorithms and methods.
common encryption algorithms and methods:
data encryption standard (des)
rivest, shamir, and adleman (rsa) encryption algorithm
triple des
diffie-hellman key exchange
elliptic curve cryptography (ecc)
blowfish
secure sockets layer (ssl)
transport layer security (tls)
advanced encryption standard (aes)
digital signature

Answers: 2


Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 16:30, nxusasmangaliso1191
The most common battery cable terminal is a that provides a large surface contact area with the ability to tighten the terminal onto the battery post using a nut and bolt.
Answers: 2

Computers and Technology, 22.06.2019 20:10, ianmartin6080
Assume that minutes is an int variable whose value is 0 or positive. write an expression whose value is "undercooked" or "soft-boiled" or "medium-boiled" or "hard-boiled" or "overcooked" based on the value of minutes. in particular: if the value of minutes is less than 2 the expression's value is "undercooked"; 2-4 would be a "soft-boiled", 5-7 would be "medium-boiled", 8-11 would be "hard-boiled" and 12 or more would be a "overcooked".
Answers: 1

Computers and Technology, 23.06.2019 23:30, huangjianhe135
The keyboard usually has six rows of keys. which of the following is not one of the key group categories? letter keys number keys control keys graphic keys
Answers: 1

Computers and Technology, 24.06.2019 07:40, daebreonnakelly
What type of multimedia are live news feeds? live news feeds are examples of multimedia.
Answers: 2
You know the right answer?
Match common encryption algorithms and methods with the scenarios representing real-world business a...
Questions in other subjects:

Mathematics, 25.09.2021 23:10

Mathematics, 25.09.2021 23:10

World Languages, 25.09.2021 23:10

Mathematics, 25.09.2021 23:10


History, 25.09.2021 23:10


Mathematics, 25.09.2021 23:10

Social Studies, 25.09.2021 23:10