cyber security network problem
problem overview
you have just moved into a new...

Computers and Technology, 02.12.2019 02:31 popa60
cyber security network problem
problem overview
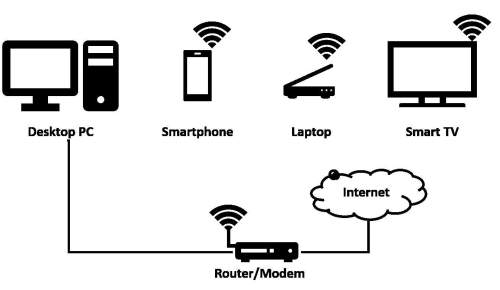
you have just moved into a new home, and you have brought all your digital communications devices. after contacting your internet service provider and getting connected, you now need to secure this home environment. review the diagram below of all the devices, mobile and stationary.
problem requirements
1. all devices must be protected against intrusion from other people
2. devices must be secure against malware
3. people using the devices must be security aware
4. internet access must be secure from unauthorized access and/or intrusion
5. all devices must be up-to-date and properly functioning
6. all critical data must be recoverable in the event of failure
7. the digital communications environment must be safe to use and defended
problem-solving process:
only do the discover and design stages of problem-solving.
stage 1: discover
during this stage the problem is defined in detail. the scope of the problem is stated so that it is clear why this problem is important. the impact and risks of the problem are evaluated so that each risk is named with its likelihood of occurring and its level of severity. actions are assigned to each risk that will reduce or resolve it. finally, all the people that are affected are identified giving a clear declaration of their level of involvement with the problem.
stage 2: design
in this design stage possible solutions are proposed and evaluated. each alternative approach to solving the problem is identified and discussed. a method is defined to evaluate each alternative solution. alternative solutions should be both creative and reasonable. the recommended solution is chosen and stated clearly explaining why this alternative is the best one.
questions to consider:
use these and other questions to develop and design your solution. these are not questions to answer directly in your submissions but only to you solve the problem.
1. how will the security solution be used and by whom?
2. are devices protected from unauthorized use and intrusion?
3. are the people using the devices cyber-security aware?
4. can the data on the devices be recovered?
5. is the environment defended against malware?
6. what documentation and planning prepare for security problems?
7. is the internet use safe from intrusion?
8. does your solution solve the whole problem for all the people involved
divide the problem solution in two sections, discover and design, addressing at minimum each of the items listed below. use headers to clarify what part of the problem you are addressing. consider using a table or spreadsheet for your risk analysis.
1. discover document
a. problem definition
i. full problem statement
ii. scope of problem
iii. impact and risks of problem giving at least five risks, their likelihood, and actions to reduce each risk.
iv. people affected
2. design document
a. design statement
i. identify at least ten steps to take to secure this environment and all the devices
ii. explain the value and importance of each step you propose
iii. identify at least five security criteria and evaluate/score your solution by these criteria
iv. state why your solution is effective and reasonable.

Answers: 1


Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 22:10, Metlife
Asequential circuit contains a register of four flip-flops. initially a binary number n (0000 ≤ n ≤ 1100) is stored in the flip-flops. after a single clock pulse is applied to the circuit, the register should contain n + 0011. in other words, the function of the sequential circuit is to add 3 to the contents of a 4-bit register. design and implement this circuit using j-k flip-flops.
Answers: 1

Computers and Technology, 23.06.2019 06:20, kiarakagni
What is a point-in-time measurement of system performance?
Answers: 3

Computers and Technology, 23.06.2019 12:40, melaniem50
Curriculum exam to process a resident's payment, you must click on onesite payments home page. from the a. reports b. my settings o c. transactions o d. rent tab
Answers: 1

Computers and Technology, 23.06.2019 15:00, victordhernandez01
Jake really works well with numbers and is skilled with computers but doesn't work well with others. which of the jobs discussed in this unit might be best for jake? why?
Answers: 3
You know the right answer?
Questions in other subjects:


Law, 12.12.2020 15:50

Biology, 12.12.2020 15:50

Mathematics, 12.12.2020 15:50



Mathematics, 12.12.2020 15:50

Mathematics, 12.12.2020 15:50




